Adding my existing Centos Box to also authenticate to my LDAP Server
On the Centos Box, I have the following package installed:
openldap-2.2.13-4
nss_ldap-226-10
compat-openldap-2.1.30-4
openldap-clients-2.2.13-4
On this box, I dont have X running so all the configuration is via CLI. To start with, I open the konsole, log as root then run
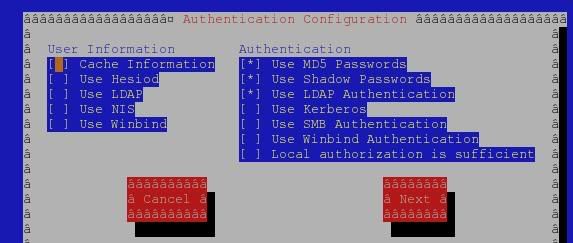
ok, on my box, after doing that, It should automatically touch and modified /etc/nsswitch.conf but it did'nt (or maybe I'm wrong), so I manually modified that /etc/nsswitch.conf
passwd: files ldap
shadow: files ldap
group: files ldap
I added the word
Below are my working config files, which also allows ldap users to change their own password using the command passwd:
/etc/pam.d/system-auth
#%PAM-1.0
# This file is auto-generated.
# User changes will be destroyed the next time authconfig is run.
auth required /lib/security/$ISA/pam_env.so
auth sufficient /lib/security/$ISA/pam_unix.so
auth sufficient /lib/security/$ISA/pam_ldap.so likeauth nullok use_first_pass
auth required /lib/security/$ISA/pam_deny.so
account required /lib/security/$ISA/pam_unix.so broken_shadow
account sufficient /lib/security/$ISA/pam_succeed_if.so uid < 100 quiet
account sufficient /lib/security/$ISA/pam_ldap.so
#account [default=bad success=ok user_unknown=ignore] /lib/security/$ISA/pam_ldap.so
account required /lib/security/$ISA/pam_permit.so
password requisite /lib/security/$ISA/pam_cracklib.so retry=3
password sufficient /lib/security/$ISA/pam_unix.so nullok use_authtok md5 shadow
password sufficient /lib/security/$ISA/pam_ldap.so use_authtok
password required /lib/security/$ISA/pam_deny.so
session optional /lib/security/$ISA/pam_mkhomedir.so skel=/etc/skel/ umask=0022
session required /lib/security/$ISA/pam_limits.so
session required /lib/security/$ISA/pam_unix.so
session optional /lib/security/$ISA/pam_ldap.so
and my /etc/pam.d/passwd file
#%PAM-1.0
#auth required pam_stack.so service=system-auth
#account required pam_stack.so service=system-auth
#password required pam_stack.so service=system-auth
password sufficient pam_ldap.so
password required pam_unix.so nullok obscure min=4 max=8
and my /etc/ldap.conf
#I'm using stunnel, so the value of host should be localhost
host 127.0.0.1
base dc=duriancity,dc=dvo
ldap_version 3
scope one
pam_filter objectclass=posixaccount
pam_login_attribute uid
pam_member_attribute gid
pam_password crypt
nss_base_passwd dc=duriancity,dc=dvo?sub
nss_base_passwd ou=People,dc=duriancity,dc=dvo?one
nss_base_shadow dc=duriancity,dc=dvo?sub
nss_base_group dc=duriancity,dc=dvo?sub
ssl no
and create the file /etc/stunnel/stunnel.conf
chroot = /home/stunnel
pid = /stunnel.pid
setuid = stunnel
setgid = stunnel
#configure logging
debug = 7
output = /var/log/messages
#client mode
client = yes
#Service level config
[ldap]
accept = 389
connect = 172.16.0.250:636
then create the user stunnel and then lock that user
To test if its working, issue the command
getent passwd
It should display the ldap users together with other existing local users


0 Comments:
Post a Comment
<< Home