The scenario:
1. Setup an OpenLDAP server for Central authentication of Linux Users.
2. Let users change their password from client PC using the normal passwd command
3. The LDAP server resides at Centos Box
4. The client PCs are mandriva, or mix later
-------------------------------------------------
1. Install and Setup OpenLDAP server on Centos.
the following openldap packages installed on my Centos BOX
openldap.i386 2.2.13-4 installed
openldap-clients.i386 2.2.13-4 installed
openldap-devel.i386 2.2.13-4 installed
openldap-servers.i386 2.2.13-4 installed
Files and folders to remember
- /etc/openldap/slapd.conf - configuration files
- /etc/ldap.conf - clients conf file
- /usr/share/openldap/migration/ - migration tools here
- /var/lib/ldap/ - default location where the dtabase be installed
Now on my system, I install LDAP via yum, so it uses the RPM package of Centos.
Here's the contents of my /etc/openldap/slapd.conf
#
# See slapd.conf(5) for details on configuration options.
# This file should NOT be world readable.
#
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/nis.schema
#
#Define ACL
#include /etc/openldap/slap.acl.conf
# Allow LDAPv2 client connections. This is NOT the default.
allow bind_v2
#
loglevel 296
pidfile /var/run/slapd.pid
argsfile /var/run/slapd.args
#
#Below allows users to change their own password
access to attr=userPassword
by self write
by anonymous auth
by dn.base="cn=ldapadmin,dc=duriancity,dc=dvo" write
by * none
access to *
by self write
by dn.base="cn=ldapadmin,dc=duriancity,dc=dvo" write
by * read
#
database ldbm
suffix "dc=duriancity,dc=dvo"
rootdn "cn=ldapadmin,dc=duriancity,dc=dvo"
rootpw {SSHA}pgsjjjklsfghrrhh53644fhmd85utuegjH3NM+DJH569XZc
#
#The duriancity.dvo directory had been manually created then changed its ownership to ldap
directory /var/lib/ldap/duriancity.dvo
#
#RW file mode defined
mode 0600
# Indices to maintain for this database
index objectClass,uid,uidNumber,gidNumber,memberUid eq
#
#End of Config File
Generating the rootpw:
Open a konsole then issue the command as root:
[root@linux-ldap-server ~]# slappasswd
New password:
Re-enter new password:
{SSHA}pgsjjjklsfghrrhh53644fhmd85utuegjH3NM+DJH569XZc
Then make sure ldap run as a service.
chkconfig ldap on
then start the service
/etc/init.d/ldap start
by default, it should listen to port 389
---------------------------------------------------------
Some basic explanation:
-
loglevel = 296 - logging level is set to 296, which equals 8 + 32 + 256 (got this from Oreilly Book)
Defination:
8 - Connection management
32 - Search filter processing
256 - Statistics for connection, operations, and results
OpenLDAP Logging levels Table
Level Information recorded
-1 All logging information
0 No Logging information
1 Trace function calls
2 Packet-handling debugging information
4 Heavy trace debugging
8 Connection management
16 Packets sent and received
32 Search filter processing
64 Configuration file processing
128 Access control list processing
256 Statistics for connection, operations, and results
512 Statistics for results returned to clients
1024 Communication with shell backends
2048 Print entry parsing debug information
then append
local4.debug /var/log/slapd.log
on the file
/etc/syslog.conf
and by that, you can view the logs by the command, as root:
tail -f /var/log/slapd.log
-
cn=ldapadmin - it could be any name, root, admin, but the default is Manager
-
rootpw - the value could be generated by the command slappasswd
Now, I need to create an ldif file for duriancity.dvo, below is the format
#/etc/openldap/duriancity.dvo.ldif
dn: dc=example,dc=com
dc: example
description: Root LDAP entry for example.com
objectClass: dcObject
objectClass: organizationalUnit
ou: rootobject
dn: ou=People, dc=example,dc=com
ou: People
description: All people in organisation
objectClass: organizationalUnit
#-------------------------------
then add or import it on ldap database by the command below:
ldapadd -x -D "cn=ldapadmin,dc=duriancity,dc=dvo" -W -f /etc/openldap/duriancity.dvo.ldif
Now, I will add a group ldaptestusers and a user ldapuser1002 which is a member of ldaptestusers group.
-----------------------------------------------------------------
[root@cicdavao ~]# groupadd -g 10700 ldaptestusers
[root@cicdavao ~]# useradd -u 10505 -g ldaptestusers ldapuser1002
[root@cicdavao ~]# passwd ldapuser1002
Changing password for user ldapuser1002.
New UNIX password:
Retype new UNIX password:
passwd: all authentication tokens updated successfully.
Now I have to migrate the ldaptestusers group and ldapuser1002 and import it to ldap database
[root@cicdavao ~]# grep ldaptestusers /etc/group
ldaptestusers:x:10700:
[root@cicdavao ~]# grep ldaptestusers /etc/group > /etc/openldap/ldaptestusers.group.tmp
[root@cicdavao ~]# /usr/share/openldap/migration/migrate_group.pl /etc/openldap/ldaptestusers.group.tmp > /etc/openldap/ldaptestusers.group.ldif
[root@cicdavao ~]# cat /etc/openldap/ldaptestusers.group.ldif
dn: cn=ldaptestusers,ou=Group,dc=duriancity,dc=dvo
objectClass: posixGroup
objectClass: top
cn: ldaptestusers
userPassword: {crypt}x
gidNumber: 10700
[root@cicdavao ~]# ldapadd -x -D "cn=ldapadmin,dc=duriancity,dc=dvo" -W -f /etc/openldap/ldaptestusers.group.ldif
Enter LDAP Password:
adding new entry "cn=ldaptestusers,ou=Group,dc=duriancity,dc=dvo"
[root@cicdavao ~]# grep ldapuser1002 /etc/passwd
ldapuser1002:x:10505:10700::/home/ldapuser1002:/bin/bash
[root@cicdavao ~]# grep ldapuser1002 /etc/passwd > /etc/openldap/ldaptestuser1002.passwd.tmp
[root@cicdavao ~]# /usr/share/openldap/migration/migrate_passwd.pl /etc/openldap/ldaptestuser1002.passwd.tmp > /etc/openldap/ldaptestuser1002.passwd.ldif
[root@cicdavao ~]# cat /etc/openldap/ldaptestuser1002.passwd.ldif
dn: uid=ldapuser1002,ou=People,dc=duriancity,dc=dvo
uid: ldapuser1002
cn: ldapuser1002
sn: ldapuser1002
mail: ldapuser1002@duriancity.dvo
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: {crypt}$1$Hl8WW1s8$tKiKrYmOT/Vy6G9yitrLp/
shadowLastChange: 13371
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 10505
gidNumber: 10700
homeDirectory: /home/ldapuser1002
[root@cicdavao ~]# ldapadd -x -D "cn=ldapadmin,dc=duriancity,dc=dvo" -W -f /etc/openldap/ldaptestuser1002.passwd.ldif
Enter LDAP Password:
adding new entry "uid=ldapuser1002,ou=People,dc=duriancity,dc=dvo"
-----------------------------------------------------
After doing the above, I have now an ldapuser1002 which had been already exported at the ldap database. It should now be able to login at the client assuming its been properly configured to auth to ldap server.
Now here's my ldap.conf on the ldap server:
#/etc/ldap.conf
host 127.0.0.1
base dc=duriancity,dc=dvo
ssl no
tls_cacertdir /etc/openldap/cacerts
pam_password md5
#------------------
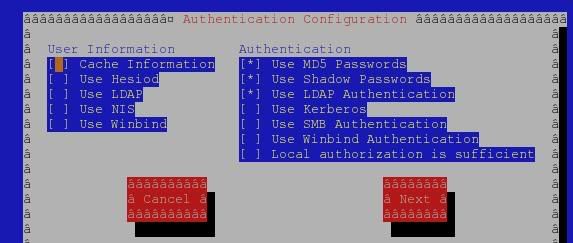
Now, configuring the client PC which is Mandriva LE 2005 and 2006On my Box, I open up a console then run
Drakauth
as root, then select LDAP and enter the necessary info, which are:
server and base DN
Here's my /etc/ldap.conf on my Mandriva Box acting as client, I just deleted the lines that has been commented out.
host 172.16.0.253
#host 127.0.0.1
# The distinguished name of the search base.
base dc=duriancity,dc=dvo
# The LDAP version to use (defaults to 3
# if supported by client library)
ldap_version 3
# The port.
# Optional: default is 389.
#port 389
# The search scope.
#scope sub
scope one
#scope base
# Search timelimit
#timelimit 30
# Filter to AND with uid=%s
pam_filter objectclass=posixaccount
# The user ID attribute (defaults to uid)
pam_login_attribute uid
# Group member attribute
pam_member_attribute gid
pam_password crypt
nss_base_passwd dc=duriancity,dc=dvo?sub
nss_base_passwd ou=People,dc=duriancity,dc=dvo?one
nss_base_shadow dc=duriancity,dc=dvo?sub
nss_base_group dc=duriancity,dc=dvo?sub
# OpenLDAP SSL mechanism
# start_tls mechanism uses the normal LDAP port, LDAPS typically 636
#ssl start_tls
ssl off
and my /etc/pam.d/system-auth and /etc/pam.d/passwd
#/etc/pam.d/system-auth
#%PAM-1.0
auth required pam_env.so
auth sufficient pam_unix.so
auth sufficient pam_ldap.so likeauth nullok use_first_pass
auth required pam_deny.so
account sufficient pam_unix.so
account sufficient pam_ldap.so use_first_pass
account required pam_deny.so
password required pam_cracklib.so retry=3 minlen=2 dcredit=0 ucredit=0
password sufficient pam_unix.so nullok use_authtok md5 shadow
password sufficient pam_ldap.so
password required pam_deny.so
session optional pam_mkhomedir.so skel=/etc/skel/ umask=0022
session required pam_limits.so
session required pam_unix.so
session optional pam_ldap.so
#--------------------------------------
#/etc/pam.d/passwd
password sufficient pam_ldap.so
password required pam_unix.so nullok obscure min=4 max=8
#--------------------------------------
and here's also my /etc/nsswitch.conf, very imortant file that for the system to look for ldapserver for authentication...
#
# /etc/nsswitch.conf
#
# An example Name Service Switch config file. This file should be
# sorted with the most-used services at the beginning.
#
# The entry '[NOTFOUND=return]' means that the search for an
# entry should stop if the search in the previous entry turned
# up nothing. Note that if the search failed due to some other reason
# (like no NIS server responding) then the search continues with the
# next entry.
#
# Legal entries are:
#
# nisplus or nis+ Use NIS+ (NIS version 3)
# nis or yp Use NIS (NIS version 2), also called YP
# dns Use DNS (Domain Name Service)
# files Use the local files
# db Use the local database (.db) files
# compat Use NIS on compat mode
# hesiod Use Hesiod for user lookups
# [NOTFOUND=return] Stop searching if not found so far
#
# To use db, put the "db" in front of "files" for entries you want to be
# looked up first in the databases
#
# Example:
#passwd: db files nisplus nis
#shadow: db files nisplus nis
#group: db files nisplus nis
passwd: files ldap nisplus
shadow: files ldap nisplus
group: files ldap nisplus
#hosts: db files nisplus nis dns
hosts: files nisplus nis dns
# Example - obey only what nisplus tells us...
#services: nisplus [NOTFOUND=return] files
#networks: nisplus [NOTFOUND=return] files
#protocols: nisplus [NOTFOUND=return] files
#rpc: nisplus [NOTFOUND=return] files
#ethers: nisplus [NOTFOUND=return] files
#netmasks: nisplus [NOTFOUND=return] files
bootparams: nisplus [NOTFOUND=return] files
ethers: files
netmasks: files
networks: files
protocols: files
rpc: files
services: files
netgroup: nisplus
publickey: nisplus
automount: files ldap nisplus
aliases: files nisplus
By the above config, assuming that no firewall related problem, the ldapusers are able to login from the MandrivaBox either using KDE or via konsole...
ex..
[ken@nixbox ~]$ su ldapuser1002
Password:
Creating directory '/home/ldapuser1002'.
bash-3.00$ id
uid=10505(ldapuser1002) gid=10700(ldaptestusers) groups=10700(ldaptestusers)
bash-3.00$ passwd
Changing password for user ldapuser1002.
Enter login(LDAP) password:
New password:
Re-enter new password:
LDAP password information changed for ldapuser1002
passwd: all authentication tokens updated successfully.
bash-3.00$
The above shown that ldapusers1002 been able to log using su command from mandriva Box that has been properly configured to auth to Ldap Server.
The user also been able to use the passwd util and change its own LDAP passsword from the Mandriva Box.
Basically Basics :D , no SSL or TLS or even stunnel yet..
I really need to post how I did it because I'll have to repeat the process on my other machine, maybe on later time, I'll become more familiar on other implementation of OpenLDAP.
Update - Configuring stunnel
On the client box which is Mandriva1. Install stunnel, as root do the ff:
urpmi stunnel
http://anorien.csc.warwick.ac.uk/mirrors/Mandrakelinux/official/2005/i586/media/main/stunnel-4.07-1mdk.i586.rpm
installing stunnel-4.07-1mdk.i586.rpm from /var/cache/urpmi/rpms
Preparing... #############################################
1/1: stunnel #############################################
To build a new pem, execute the following OpenSSL command:
openssl req -new -x509 -days 365 -nodes -config /usr/share/doc/stunnel-4.07/stunnel.cnf -out /etc/ssl/stunnel/stunnel.pem -keyout /etc/ssl/stunnel/stunnel.pem
2. Create a user named stunne with home /home/stunnel
useradd -d /home/stunnel stunnel
3. Edit stunnel.conf, on Mandriva, the stunnel.conf should be place to /etc/ssl/stunnel/ dir. Below is my stunnel.conf, by creating it manually.
chroot = /home/stunnel
pid = /stunnel.pid
setuid = stunnel
setgid = stunnel
#configure logging
debug = 7
output = /var/log/messages
#client mode
client = yes
#Service level config
[ldap]
accept = 389
connect = 172.16.0.254:636
#172.16.0.254 here is my ldapserver
Then edit also /etc/ldap.conf, make it listen to localhost
# Your LDAP server. Must be resolvable without using LDAP.
#host 172.16.0.254
host 127.0.0.1
# The distinguished name of the search base.
base dc=duriancity,dc=dvo
I change the listening host to 127.0.0.1 or localhost from its original ip. The traffic here that passes to port 389 has been redirected to 636 via secure tunnel.
4. start stunnel with the command below
stunnel
5. Then make it start as the pc boot. Edit /etc/rc.d/rc.local and append below
/usr/sbin/stunnel
6. Log can be check by the command
tail -f /var/log/messages
or if how its been defined on the stunnel.conf file.
On the Server side1. Create also a user named stunnel
2. Install stunnel if not yet installed.
3. Edit the stunnel.conf file, default config dir is /etc/stunnel/ and below are the contents on my Box.
chroot = /home/stunnel/
pid = /stunnel.pid
setuid = stunnel
setgid = stunnel
debug = 7
output = /var/log/messages
#
client = no
cert = /usr/share/ssl/certs/stunnel.pem
key = /usr/share/ssl/certs/stunnel.pem
#
[ldap]
accept = 636
connect = 389
3. Change dir to /usr/share/ssl/certs/ and issue the command below..
make stunnel.pem
4. Modify permission on stunnel.pem
chmod 640 stunnel.pem && chgrp stunnel stunnel.pem
5. start stunnel
stunnel
6. Then make it run as the pc Boot by putting it on the file /etc/rc.d/rc.local
/usr/sbin/stunnel
7. Logfile, same as above...
References:
http://www.erikberg.com/notes/auth.html
http://ldots.org/ldap/
http://www.openldap.org/doc/admin23/slapdconfig.html#Configuration%20File%20Example
http://www.oreilly.com/catalog/ldapsa/
http://www.saas.nsw.edu.au/solutions/ldap.html